- Check this post for a breakdown of the time I spent studying for the exam.
- Check this post for general tips and tricks for the exam and its preparation.
- Check this post my methodology for report writing for the exam.
Introduction
Today, July 18th, 2024, I finally got the much-awaited email from Hack The Box confirming that I passed the Certified Penetration Testing Specialist (HTB CPTS) exam with thirteen out of fourteen flags! This post is to celebrate this achievement, share why I’m so excited about getting this certification, and talk about what the experience was like and what I learned from it.
What is HTB CPTS?
THe HTB CPTS exam is a practical test designed for intermediate penetration testers. To qualify, you must complete the Penetration Tester job-role path from Academy, a highly regarded twenty-eight module course on intermediate ethical hacking skills. This course alone is a significant challenge and greatly enhanced my offensive security abilities.
Once you complete the entire path, you can attempt the exam. The exam itself is a ten-day simulated internal penetration test against a fictional company. During this time, you must fully compromise a large corporate Active Directory environment with multiple hosts. This involves exploiting both common and custom applications, escalating privileges, searching for secrets, pivoting around, and capturing flags. In addition to that, you must produce a commercial-grade penetration test report, which is manually evaluated with high scrutiny.
All in all, it’s a tough exam that requires you to prove yourself both a skilled hacker and a professional report writer. Many who have taken both this and the OSCP, the current gold standard for penetration tester certifications, say the OSCP is easier in comparison. While both certifications are clearly valuable, the CPTS has a reputation of being especially hard.
Here are some of the reviews I considered when deciding which certification to pursue:
What did I learn?
It’s a lot to cover, so it’s hard to summarize everything, but here are what I believe to be the most crucial points:
- Rules of Engagement: Knowledge of scopes, legal constraints, and ethical guidelines.
- Methodology: Conducting a pentest in a structured and methodical manner.
- Vulnerability Assessment: Identifying and prioritizing security weaknesses.
- Web: Enumeration and exploitation of both custom-made and common applications.
- Active Directory: Enumeration and exploitation, including abusing domain trusts.
- Services: Enumeration and exploitation (e.g., SMB, FTP, MySQL, DNS, etc.).
- Privilege Escalation: Techniques for both Windows and Linux servers/workstations.
- Pillaging: Searching for valuable information after a breach for further exploitation.
- Pivoting: Using pivots in a corporate environment to bypass network restrictions.
- Data Transfer: Moving data in and out of compromised hosts stealthily and securely.
- Reporting: Producing a commercial-grade professional penetration test report.
- Mental Resilience: Adopting a determined attitude in approaching challenges.
Credly also has a nice summary of the main skills learned:
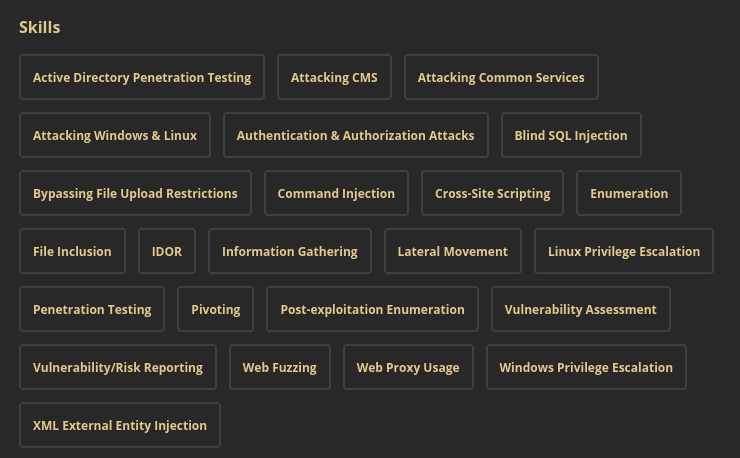
HTB's methodology for penetration testing.
For a complete overview of the material, you can check out the course page. If you’d like to dive into what I learned in more detail, keep reading, and I’ll break down each bullet point and cover the specifics.
Methodology
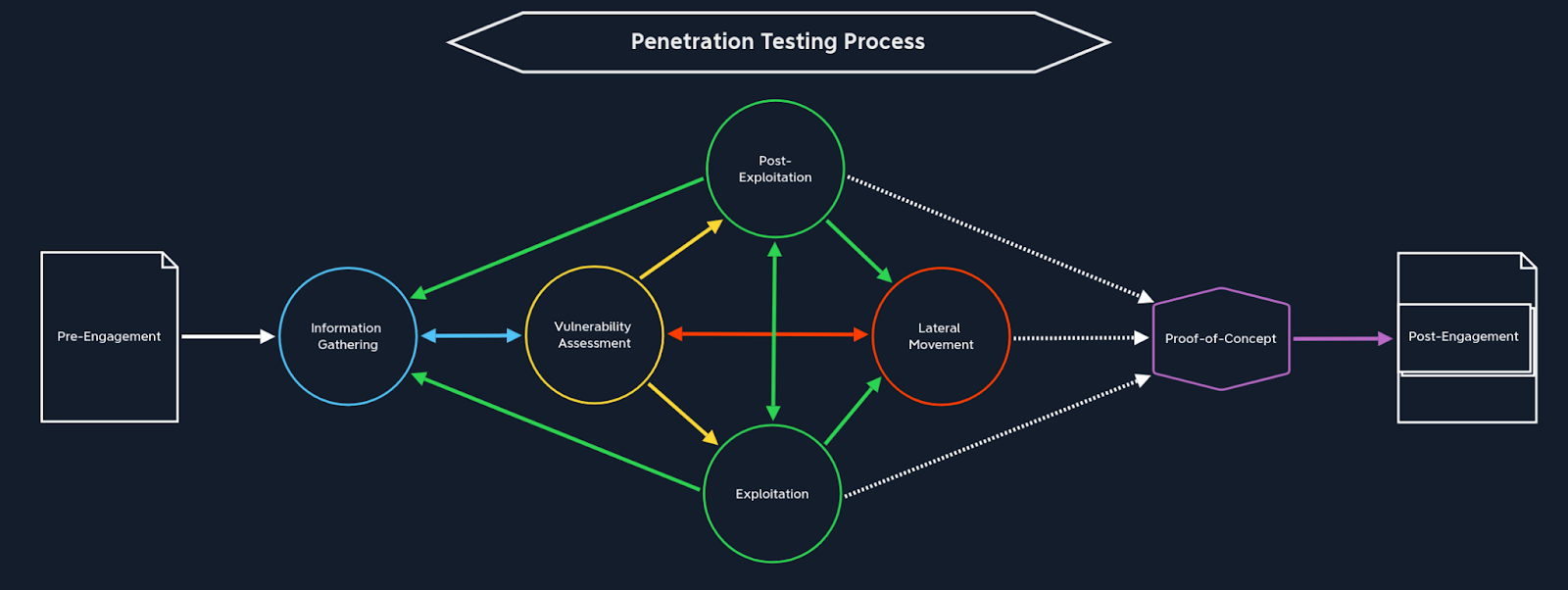
HTB's methodology for penetration testing.
The very first thing the course covered was the importance of following a robust methodology when conducting a penetration test.
It then emphasized the need for meticulous note-taking throughout the engagement and the delivery of high-quality, actionable reports to the client.
These lessons have totally changed how I see penetration testing, reminding me that success is all about having a solid process and staying professional.
Web Pentesting
Web applications usually present a huge attack surface, so a significant portion of the course was dedicated to web penetration testing. Personally, I believe this is one of my strongest areas.
To achieve this, I worked with various tools including Burp Suite, WhatWeb, FFUF, SQLmap, and more.
Common Web Applications
The course breaks down many common web applications found in corporate environments, whether they are externally or internally facing, and thoroughly explains the various ways they can be exploited.
I gained extensive experience exploiting these web applications, from enumeration and version footprinting to abusing vulnerable versions, exploiting built-in functionality, vulnerable plugins, common misconfigurations, weak default credentials, and more.
Here are some of them:
-
Content Management Systems (CMS):
- WordPress
- Joomla
- Drupal
- DotNetNuke
-
Web Servers:
- Tomcat
- ColdFusion
-
Development and Deployment Tools:
- Jenkins
- GitLab
-
Monitoring and Analytics:
- Splunk
- PRTG Network Monitor
- Nagios XI
-
Ticketing Systems:
- osTicket
Custom Web Applications
This exam goes far beyond simply identifying CVEs and finding exploit scripts online. Often, I encountered custom-made web applications and had to dig in to identify vulnerabilities myself, sometimes creating my own tools in the process.
This is where my background in Software Engineering proved invaluable. Having a deep understanding of secure application development helped me spot potential weak links in the application, giving me an insider’s perspective.
Here are some of the web vulnerabilities I became proficient at identifying and exploiting. Many of these are part of the OWASP Top Ten, highlighting their relevance:
- Reconnaissance
- Technology Stack Footprinting
- Virtual Host Enumeration
- Directory, File and Parameter Fuzzing
- Exploitation
- Cross-Site Scripting (XSS)
- Local File Inclusion (LFI)
- SQL Injection (SQLi)
- File Upload Attacks
- Command Injection
- Authorization & Authentication Attacks
- HTTP Verb Tampering
- Login Brute Forcing
- Insecure Direct Object Referencing (IDOR)
- XML External Entity (XXE)
Active Directory
Before taking the course, Active Directory was one of the topics I struggled with and felt a bit intimidated by. That’s why I made a point to really focus on it while studying, even taking extra modules outside of the course. I’m happy to say that this extra effort paid off, and now I’m confident in my understanding and skills with Active Directory.
The course had multiple modules on Active Directory, and they were all great. I got plenty of time using tools such as BloodHound to map out AD environments and identify potential attack vectors, and NetExec (formerly CrackMapExec) to perform remote command execution and gather valuable information about networked systems.
There are too many techniques covered to list them all, but here are a few highlights:
- User Enumeration
- SMB Null Authentication
- LDAP Anonymous Bind
- RID Brute Forcing
- Kerbrute (using a wordlist)
- Further Enumeration
- Password Policy (for safe password spraying)
- Security Controls (e.g. AppLocker, Defender, LAPS, etc.)
- GPP Passwords
- SYSVOL Pillaging (e.g. credential in scripts)
- Passwords In Description Fields
PASSWD_NOTREQDField (easier targets for password spraying)- SMB Shares Pillaging
- Attacks
- Kerberoasting
- ASREPRoasting
- LLMNR / NBT-NS Poisoning
- NTLMv2 Hash Stealing (e.g. malicious .lnk files)
- ACL Abuse
- GPO Abuse
- Password Spraying
- Credential Reuse
- DCSync
- noPac
- PetitPotam
- PrintNightmare
Services Enumeration & Attacks
Throughout the course and exam, I interacted with a lot of common (and less common) services on live hosts.
I learned how to identify their versions and thoroughly enumerate them using tools like Nmap, Netcat, and NetExec. I became adept at finding vulnerable versions and common misconfigurations that can be leveraged to gain a foothold into the host, disclose secret information, or otherwise benefit the engagement.
Most importantly, I gained a deep understanding of the purpose of each service, how they work under the hood, and how they can be exploited in unintended ways.
Here are some of the services I gained a lot of experience with:
- File Transfer Protocols
- SMB
- NFS
- FTP
- TFTP
- Rsync
- Remote Access and Management
- SSH
- RDP
- WinRM
- Email Protocols
- SMTP
- POP3
- IMAP
- Network Services
- DNS
- SNMP
- LDAP
- Kerberos
- R-Services
- IPMI
- Database Services
- MSSQL
- MySQL
- Oracle TNS
Local Privilege Escalation & Pillaging
Since the exam environment is a network with multiple hosts, escalating your privileges after gaining an initial foothold is a common task throughout both the course and the exam. Manual enumeration is emphasized over automated tools, requiring a thorough and hands-on approach to discover flaws.
However, something that’s less commonly practiced is the post-exploitation stage. In most CTFs, the challenge is considered complete once you achieve the highest local privilege. But in the exam, after reaching root/SYSTEM, you need to pillage the host for information that can be used to demonstrate impact to the client or leveraged to access other hosts and further compromise the domain.
Here are some of the local privilege escalation and pillaging techniques I practiced extensively:
Linux
-
Privilege Escalation Techniques
- Sudo Rights Abuse
- Privileged Group Membership (e.g. Docker, Adm, Shadow, LXC/LXD, Disk, etc.)
- SUID/GUID Executables
- Vulnerable Program Versions (e.g. sudo, screen, logrotate, etc.)
- Cron Job Exploitation
- Abusing Capabilities (e.g.
cap_chown,cap_fowner,cap_setuid, etc.) - Wildcard Injection Attacks
- Python Library Hijacking
- NFS
no_root_squashAbuse $PATHAbuse- Restricted Shell Escape
- Hijacking Shared Objects
- Taking Over Tmux Sessions
- Exploiting Writable Docker Sockets
- Kernel Exploits (e.g. PwnKit, DirtyPipe, DirtyCow, etc.)
-
Pillage Techniques
- Enumerating Distribution and Kernel Information
- Credential Hunting (e.g. history files, web configs, SSH keys, etc.)
- Browser Cookie Stealing
- Process Monitoring
- Traffic Eavesdropping
- Checking Active Directory Domain Membership
Windows
I got plenty of experience using tools like Mimikatz, Rubeus, NetExec, WinPeas, Windows Exploit Suggester, Evil-WinRM, and many others. The course also stressed the importance of living off the land as much as possible.
-
Privilege Escalation Techniques
- Access Token Abuse (e.g.
SeImpersonate,SeTakeOwnershipPrivilege, etc.) - Privileged Group Membership (e.g. Backup Operators, DnsAdmins, etc.)
- UAC Bypass
- Kernel Exploits (e.g. SeriousSAM / HiveNightmare, PrintNightmare, etc.)
- Legacy Operating System Exploitation (e.g. EternalBlue)
- Unquoted Service Paths
- Weak Service Permissions
- Scheduled Task Abuse
- Permissive Registry ACLs
- Modifiable Registry Autorun Binary
- Always Install Elevated
- Vulnerable Third Party Programs
- Malicious SCF and .Ink Files (hash stealing)
- Citrix Breakout
- VMDK, VHD, and VHDX Files
- Access Token Abuse (e.g.
-
Pillage Techniques
- Credential Hunting (e.g. SMB/NFS shares, unattend.xml, configuration files, etc.)
- Credential Sniffing
- SAM, LSA, LSASS and NTDS.dit Secret Dumping
- Browser Cookie Stealing
Pivoting & Transfer
In the exam, pivoting is key for moving from one compromised host to other systems on the network. Network restrictions, such as different subnetworks, often require turning compromised hosts into pivots to access deeper parts of the environment.
The course covered various tools for this purpose, including SSH, Chisel, and Ligolo-ng. Mastering these tools was crucial for expanding access and completing the exam’s challenges.
Similarly, file transfer techniques were essential for sending and receiving files from a compromised host while bypassing security restrictions and ensuring secure transmission.
The course covered methods such as using certutil for base64 encoding, setting up our own SMB servers, leveraging PowerShell for secure file transfers and much, much more.
Reporting
The certification isn’t just about technical hacking skills. It also focuses on thoroughly documenting findings in a professional pentesting report for clients.
Hacking is fun, but the real value for clients comes from the detailed reports. That’s why there’s a big emphasis on writing top-notch, commercial-grade reports.
In my exam feedback, the examiner praised my report, showing that I didn’t just improve as a hacker but also as a professional.
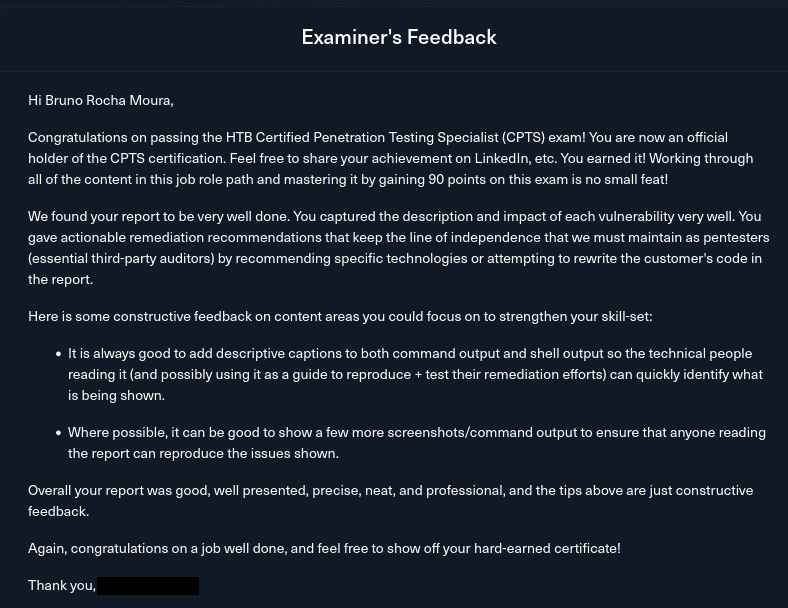
Examiner's feedback on my report.
Mental Resilience
Lastly, the exam taught me mental resilience in ways I never expected. The challenges were so tough that I often found myself stuck and frustrated, struggling to find solutions. There were moments when I felt overwhelmed and wanted to give up, but the exam demanded that I push through these barriers.
It taught me the importance of staying calm under pressure, persevering through obstacles, and maintaining a positive mindset. This experience was a valuable lesson in mental toughness, showing me that success in cybersecurity often comes down to resilience and determination as much as it does to technical skills.