- Check this post for a breakdown of the time I spent studying for the exam.
- Check this post for my overall experience on the exam and what I learned from it.
- Check this post my methodology for report writing for the exam.
Introduction & Disclaimer
Today, I’m excited to share that I passed Hack The Box’s Certified Penetration Tester Specialist (HTB CPTS) exam on my first try! This intermediate certification is a big step for me as an aspiring penetration tester. To celebrate and give back to the HTB community for all their support, I’ve put together this post with my best tips for preparing for and passing the exam.
I hope this guide helps you navigate the preparation process and boosts your chances of success. Whether you’re just starting out or in the final stretch of your study plan, I’ve included strategies and insights that worked for me and can make a real difference. Good luck!
Disclaimer: I want to make it clear that the tips and insights shared in this post are meant to be general advice and study strategies based on my personal experience with the HTB CPTS exam. I have made every effort to ensure that nothing shared here violates the exam’s rules or offers any unfair advantages. My goal is to provide helpful guidance and support for those preparing for the exam, not to disclose any specific exam content or breaches of HTB’s policies.
Tips for the preparation
Take detailed and structured notes
The best advice I got when prepping for the CPTS exam was to take extensive notes throughout the course. Having taken the exam, I can say that this was one of the most important things for doing well.
But I’ve seen people online wondering why they should bother with note-taking if the modules already have cheatsheets of commands you can look at anytime. Some folks just copy and paste these cheatsheets into text files and call it a day, thinking that’s enough. While cheatsheets are helpful and can be a good starting point, they’re not a substitute for real note-taking.
My recommendation is to create a field manual—a well-structured document with detailed notes you can consult during your engagements. Use a hierarchical note-taking app like Notion, Obsidian, Zim, or CherryTree (my personal favorite). This is far better than a plain text file because it lets you organize your notes, group related info together, and easily search and toggle visibility as needed. Besides aiding you during the exam, note-taking also forces you to engage with what you are learning, helping to reinforce your understanding and retention of the material.
At the start of the exam, my field manual was a CherryTree file with 376 nodes and 114,331 words. It organizes notes into five primary categories for the steps in the penetration tester methodology covered in the exam: Information Gathering, Vulnerability Assessment (which I renamed to Pre-Exploitation), Exploitation, Post-Exploitation, and Lateral Movement. I also created a category just for NetExec since its uses span all the categories. The notes were taken during the study of each module and filled in as I went, with some restructuring as I completed more and more modules.
The attached picture below shows the tree layout of my field manual with just one level of depth. Each node with a right-pointing arrow expands to contain more nodes, which can also contain more nodes, and so on. I won’t show the whole thing because it would be gigantic, but you get the idea.
Field manual tree
Edit: Due to popular demand, you can see the entirety of my field manual structure here.
Most of my notes were divided into two sections. At the top, there’s a cheatsheet section in the form of a table containing key information or commands ready to be copied and pasted. Below that, there’s an information section with a summary of the topic, a deeper explanation of its inner workings, diagrams or images, and links to online resources or other notes within the document. Here are my notes on the SMTP protocol as an example:
Field manual SMTP example
CherryTree allows you to search for notes by either their content, name, or tags (which you can assign to notes). For instance, if I encounter a Tomcat instance during an engagement, I can quickly press CTRL + T to search for a term in the note’s name and tags, like “exploit tomcat,” to find my note on Tomcat exploitation. Alternatively, I can navigate manually to the Tomcat node under Exploitation > Application Exploitation > Tomcat. I can also search for specific terms within a note’s content using CTRL + Shift + F.
If you have a field manual, you are never wasting time trying to remember a command by memory or juggling between browser tabs looking for the module which contains the cheatsheet with that one command you need. With a few key strokes, you land on a note with the exact information you need ready to be consulted or copy and pasted.
Consider taking some additional modules
A common tip you’ll see throughout this post is that it generally doesn’t make sense to spend too much time on extra-curricular material because the path and the exam are very closely aligned. For instance, it wouldn’t be worthwhile to dive into binary buffer overflow modules since they aren’t covered at all during the path. However, there are a few modules outside the path that I would still recommend.
First, if you’re new to CyberSec and preparing for the CPTS, I think it’s a good idea to complete the Information Security Foundations and Basic Toolset skill paths. I didn’t do them myself since I already had some experience, but I wouldn’t advise jumping straight into the CPTS path without this foundational knowledge. In fact, the path itself recommends these skill paths.
Sometimes, a module will list other modules (not necessarily part of the path) as prerequisites. For example, Attacking Web Applications with Ffuf suggests that you should have a solid grasp of the topics covered in Introduction to Networking, Linux Fundamentals, and Web Requests. If you’re already familiar with these topics, you can skip them as I did for most modules. However, if you’re not completely comfortable with these areas, I recommend doing them before moving on. I took Introduction To Active Directory and Windows Fundamentals myself, as they were recommended by Active Directory Enumeration & Attacks and I needed a refresher.
Lastly, there is one module that wasn’t mentioned in the path (that I can recall) but was highly recommended to me by my friend Pengrey: Using CrackMapExec.
This module turned out to be one of the most useful resources I used in preparation for the exam, even more so than some of the modules included in the path. NetExec (formerly CrackMapExec) is an incredibly versatile tool with numerous applications, so it’s worth learning all of them. This module is Tier III, meaning it’s not covered by the student plan. I can’t recall exactly how many cubes it took to purchase (and I can’t check the price after buying), but you can easily use the cubes you earn from completing the path. Just be aware that this module covers some techniques that are not mentioned anywhere in the path and are outside the scope of the exam. Make a note of these techniques in your notes or elsewhere so that you don’t waste time trying things that won’t be useful for the exam.
Attempt AEN blind to gauge preparedness
The path concludes with the final module, Attacking Enterprise Networks (AEN). This module is a walkthrough of an enterprise-like lab containing multiple machines, and it integrates techniques from throughout the entire path. One of the most common tips you’ll find is to try completing AEN completely blind, simulating the exam experience to gauge your readiness. I followed this advice, and I think you should too.
Attempting this module blind is the closest you’ll get to the real exam experience bar nothing, though it’s naturally scaled down and not as difficult. Once you’ve seen the module content or walkthroughs, you can’t redo it blind, so try your hardest to finish it without any external help, even if you get stuck for hours or days. This exercise will be similar to what you’ll face in the actual exam. In fact, avoid even looking at the questions you need to answer to complete the module, as these questions contain hints that you won’t get in the exam. Instead, start the lab, get the IP addresses, and dive into the hacking.
That said, AEN has a specific structure that you’re expected to follow, so it’s helpful to know the general progression. Here are some spoiler-free steps you can follow instead of referring to the module’s content:
- Get all seven web flags on
DMZ01. - Get a foothold on
DMZ01 - Get root access on
DMZ01 - Get a foothold on
DEV01 - Get root access on
DEV01 - Get a foothold on
MS01 - Get root access on
MS01 - Get root access on
DC01 - Get a foothold on
MGMT01 - Get root access on
MGMT01
Note that not all of these steps will have flags, and there are flags that aren’t necessary to complete the lab. The flags in AEN aren’t really comparable to those in the exam, so don’t try to equate the two. Complete the lab first and then go submit the actual flags.
If you manage to complete AEN completely blind in around five days or less, congratulations! You are likely well-prepared for the exam. If you found yourself needing heavy help from the walkthrough or the HTB community, you should consider refining your methodology and/or getting more practice with CTFs before attempting the exam.
If you got stuck on AEN here and there, tried hard to overcome obstacles without tips, and only glanced at write-ups or asked for small nudges, don’t worry too much. I couldn’t complete AEN completely blind either and had to take small peeks a few times to get unstuck. The goal is to try your hardest to overcome challenges without help, but you’re not really benefiting from being stuck for more than a day. Take notes on where you struggled, adjust your methodology to address these gaps, and try the module again after you’ve completed it to see if you can get through it using just your notes and methodology.
If lacking experience, do some boxes; If not, don’t bother
The single most asked question about preparing for the CPTS exam is which boxes on the main platform one should complete to be prepared. People often recommend TJNull’s OSCP list and IppSec’s Unofficial CPTS Playlist as good boxes to root before the exam. However, my sincere recommendation (which many who have passed the exam share) is that you shouldn’t really be doing any boxes outside the path if you already have sufficient CTF experience.
The boxes on the main platform weren’t designed to be compatible with the CPTS exam, so they naturally contain techniques, technologies, and scenarios that are way out of scope. Even the boxes officially recommended by the modules on the path aren’t much better because, even if they do have portions that are in scope, they likely have other parts that are totally out of scope. This way, you either have to concern yourself with learning techniques that won’t benefit you on the exam or try the box until you reach something you don’t know how to beat and stop. This is not really a great way to invest your time. I did maybe three or four HTB boxes during my exam preparation, and I did them just for fun. I didn’t need to worry about that because I already had some CTF experience from my TryHackMe days.
However, my advice flips if you have little or no CTF experience. In that case, I would advise you to try many boxes—maybe one per module in the path—and it doesn’t really matter which ones. Just pick some retired easy/medium Linux or Windows boxes and have at it. The point isn’t to learn anything new but to familiarize yourself with the feel of doing an unguided box and conducting research on your own when you encounter something unfamiliar. If the box contains something covered in the path, then as a bonus, you get to test your methodology against it.
In short, I wouldn’t recommend stressing too much about boxes, ProLabs, or anything of the sort, even if officially recommended by the course, unless you are lacking in CTF experience.
Bullet-proof your methodology before the exam
Alongside taking good notes during the course, the most important thing you can do to succeed on the exam is to have a strong methodology for the different scenarios covered in the path. By methodology, I mean a written document detailing the relevant methods for a specific scenario, helping you track what you should do and when, as well as what you’ve already tried. In other words, you should define an algorithm of sorts—a set of clear instructions that, if followed blindly, would eventually lead you to overcome whatever obstacle you’re facing.
For example, you should have a methodology for Linux privilege escalation, detailing all the different things to check, techniques to try, and information to gather to find a misconfiguration or vulnerability that allows you to get root on the host. This principle can be applied to any scenario, from Active Directory attacks to Web Footprinting.
If the scenario lends itself to checklists, create one. This makes it simple to track what you need to do and what you have done in that scenario. If it’s more complex, you can design a more freeform guide that still aids you in navigating the scenario. I’ll repeat myself: your methodology should be such that if you blindly followed it in any occurrence of this scenario during the path’s practical assignments, you would succeed.
Below is the methodology for the Drupal web application that I have in my note-taking template for pentests. Notice that methodologies don’t have to be long or super descriptive—that’s what your detailed notes are for. The point of methodologies is just to guide you. There are tons of methodologies in this file, not just the ones under the methodology node, but also in other places such as the Service node and inside the host templates.
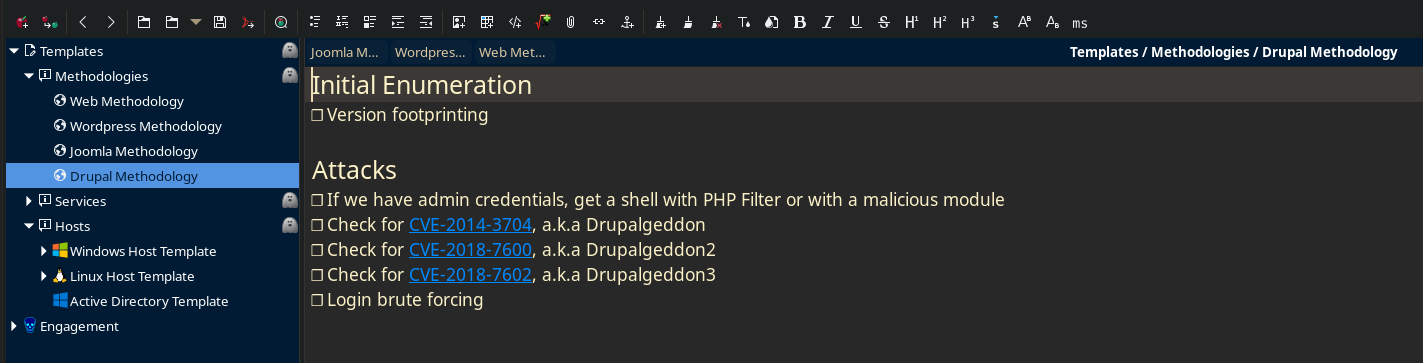
Methodology example
It’s hard to overstate how important having strong methodologies is. If you take nothing else from these tips, please create a checklist for as many scenarios as you can think of. Apply these methodologies to occurrences of their scenarios in the skill assessments and AEN to see if you can clear them by following your guide. Make your methodologies as perfect as you can, because they are likely the difference between passing and being stuck for days and failing.
Watch IppSec’s CPTS playlist
As I mentioned earlier, I don’t think it’s a good investment to spend a lot of time doing random HTB boxes to prepare for the exam, as they often include out-of-scope techniques and technologies. However, I do recommend checking out IppSec’s playlist of walkthroughs for boxes he considers to be in line with the exam. You can work through these boxes if you have the time and feel like you need the extra practice, but just watching the videos is also beneficial.
While you watch the walkthroughs, follow this exercise to get the most out of them: at every step of the pentest, ask yourself what you would do next if you were working on the box. If the next step in the walkthrough involves a technique or approach that wasn’t covered in the path, make a mental note of it and move on. But if the intended move was something you learned in the path material, ask yourself if you would have thought to try it on your own. If you realize you might have missed that step, it’s a sign that you need to refine your methodology.
Do this for every box in the playlist as a kind of stress test for your methodology. It’s an excellent way to see if your approach is solid and to identify any gaps in your process.
Don’t skip this exercise. Even seemingly unimportant or out-of-scope techniques might come in handy during the exam or in future pentests. I know I would have struggled harder at the exam had I not watched it.
Tips for the exam
The exam will not stray far from the material, but beware
As mentioned earlier, students often look for extra study materials outside the course to get ready for the exam. This usually comes in the form on:
- Active and retired HTB machines
- ProLabs
- Other CTF platforms such as TryHackMe and PentesterLab
- Resources from other courses like OSCP
This is generally not a good idea. The exam is designed to match the course path, so new techniques or information from these extra resources probably won’t be on the exam. While learning new stuff is always good, it’s important to do it at the right time. Studying irrelevant information can waste valuable time and brain power that could be used on exam-specific content. Plus, this info might confuse you during the exam, leading you to try techniques that won’t work because they’re out of scope.
However, the advice that “everything you need for the exam is on the path” can also be misleading. If you expect the exam to only include scenarios you’ve seen in the course practical assignments, you might struggle. The course teaches you to think outside the box and do your own research during pentests, and that’s expected in the exam too. Be ready to handle brand new scenarios that are still tangentially related to the course material.
In short, stick to the course path for studying, but be prepared to face unfamiliar scenarios in the exam.
Take all the time off you can
I captured the twelfth flag about seven days and ten hours after starting the exam. Twenty-two hours later, early evening on the ninth day, I submitted my report and finished the exam with almost a whole day left. If I hadn’t hit some really dumb roadblocks, I maybe could’ve shaved off a whole day from that.
Passing on the first try with over a day to spare might sound like it was easy, but it definitely wasn’t. For those ten days, I did nothing but work on the exam and do basic chores to stay alive and keep working. Seriously, I spent over 90% of my waking hours on the exam. I don’t think I would’ve passed if I had to juggle work or school too.
I highly recommend taking as much time off work or school as you can to focus on this exam. Ten days was enough time to me, but just barely. It gives you a bit of breathing room to take breaks, but you’ll still need to keep a tough pace to stay on track.
Don’t forget to eat, drink and rest
This advice is kind of trite, so I won’t dwell on it. If you’re serious about passing the exam, you’ll want to dedicate all available time to it. However, it’s easy to neglect your basic needs, like eating, drinking, and resting, when you’re focused. Remember, being hungry, thirsty, and tired won’t help your performance. Take care of yourself first so you’re in good shape to tackle the exam.
Here are some practical tips if you, like me, don’t want to even think about cooking during an exam. If you have friends or family willing to cook for you, that’s ideal. If not, or if you don’t want to burden anyone, consider meal prepping before the exam. Or stock up on ingredients for quick, nutritious meals. I’m not usually a sandwich person, but I must have made about thirty during the ten days. You could also order food every day if you are made of money.
Keep a large bottle of water with you to stay hydrated. Drink caffeinated beverages if that’s your thing. Take regular breaks. Even if you usually don’t feel the effects of long computer sessions, like me, you might after ten days. My shoulder felt strained from overuse. I wish I had used a Pomodoro timer to remind myself to take breaks, walk around the house, and stretch.
Write the report as you go
I dedicated an entire post to reporting for the CPTS exam, so I won’t dwell on it here. I strongly recommend that you write the report as you go and not leave it all until the end. Additionally, I don’t think making a rough draft of the compromise walkthrough as you go and formalizing it into the actual report at the end is a much better idea either.
Instead, develop a trigger-based approach to writing the report. With this approach, you stop and fill in the relevant parts of the report when certain “triggers” occur during the pentest, i.e. compromising a host. This way, when you finally beat the lab (or get the minimum number of flags), your report will be more than 90% complete, and you’ll just need to polish it a bit.
The exam is not AEN part II
Earlier, I pointed out that AEN is the closest thing you’ll find to the actual exam. Nothing else, including CTF boxes, ProLabs, or other certification exams, comes close. Practicing with the AEN lab under exam-like conditions (going in blind and sticking to time limits) is a great way to measure how prepared you are.
However, remember that AEN and the exam are two different things made with different goals in mind. Use AEN to check if your methodology works and to see how ready you are, but once the exam starts, forget about AEN. Don’t think of the exam as AEN 2.0. If you start doubting an approach because it didn’t work in AEN, think again. And if you’re sure something should work because it did in AEN, keep in mind that this might not be the case here.
Let go of any preconceived ideas from your AEN experience. Treat the exam like a fresh start.
Beware of common roadblocks
Everyone has their own strengths and weaknesses, so it’s expected to face challenges with different parts of the exam. However, flag one and flag nine are particularly notorious for causing trouble. These two flags are the main “filters” of the exam, and if you manage to clear both, you’re statistically likely to achieve the minimum requirement of twelve flags.
I’ve often heard on the CPTS Discord channel that the average time to get the first flag is two to three days. While this might be reassuring for those struggling with the initial parts of the exam, I have to be honest—I doubt the accuracy of this claim. This statistic is not official but rather anecdotal, based on how long people say it took them to get the first flag. Many users go to the Discord server to celebrate their milestones, posting things like, “After three long days, I finally got flag one.”
Because of this, I believe we might be seeing a form of reverse survivorship bias. We’re considering the reports from everyone who has claimed the first flag without knowing whether they passed the exam. When I spoke to people who have actually passed the exam, I noticed that most of them didn’t take more than a day to get the first flag. For me, it took just over four hours. My conclusion is that flag one isn’t necessarily a hard flag; it just seems that way because it filters out those who aren’t fully prepared. If you’re struggling with it, take a deep breath and stay positive. If you’ve paid attention to the course material, you’ll get through it.
Flag nine is considered by pretty much everyone to be the hardest portion of the exam. I don’t mean to scare anyone, but the vast majority of people who pass the first flag and still fail the exam do so at flag nine. Don’t let it intimidate you or become a bigger problem than it really is. It’s not a Herculean task, just a more challenging flag that you can overcome with proper preparation, mental focus, and creativity.
Please don’t be discouraged by what I said if you’re struggling with any part of the exam. Although it didn’t take me long to get the first flag and I captured flag nine after some struggle, I was stuck for days on a very unassuming flag that most people who have passed consider one of the easiest in the exam. Don’t worry about not meeting some arbitrary standard. The best anyone can do is their best, and if that’s what you’re doing, you have nothing to stress over.

Be comfortable in being stuck
The exam is tough, so you should expect to get stuck often, sometimes for days at a time. You might make progress at a snail’s pace, or you could end up banging your head against the wall for hours or even days with no progress at all.
It’s easy to get discouraged in these situations. With so much on the line and the clock ticking, not making any headway can make you feel desperate and anxious. I went through this myself when I was stuck at the 12th flag for three days, feeling like I might fail at the very last step after getting so far. It’s important to be ready both mentally and technically for these kinds of challenges. I’m not really the best person to give advice on handling anxiety or mental health, but I can offer some technical tips.
I’ve already talked about the importance of having a written methodology for different scenarios, ideally in the form of checklists you can use to track the techniques you’ve tried and those you haven’t. In theory, if you had flawless methodologies and unwavering focus and attention, you would never get stuck on the exam. Naturally, perfection isn’t achievable, so you’ll likely find yourself stuck at various points. When that happens, remind yourself that it’s either because your methodology is lacking, some crucial information is slipping by you, or you need to do some research around a topic.
If you’re still stuck after following your methodology, it’s time to reference the path material, as you might have missed something when making it. Use the Academy search feature to quickly look up modules containing your search terms. You can also check specific modules relevant to the scenario you’re facing. Be sure to review both the cheatsheets and the full content.
While it’s generally not a good idea to repeat the same exact technique over and over, there are times when it can be helpful to try every technique at least twice if you’re running out of ideas. There are many technical reasons why a technique might not work the first time, so keep that in mind. It can also be useful to try the same technique but with different parameters, wordlists, or protocols. Make sure to keep detailed notes on what you’ve already tried, including all the parameters you used.
If that doesn’t work, consider doing some online research related to your scenario. Be careful of getting lost in rabbit holes, as you might chase paths that aren’t relevant to the exam and lead nowhere.
If you’ve tried all this and still aren’t making progress, take a break. Go for a walk, exercise, or clear your head in some way. When you’re ready, return with a fresh mindset and start over from your methodology. Let go of preconceived assumptions and leave no stone unturned.
Use ChatGPT, but don’t turn your brain off
There’s some debate about using ChatGPT for research during exams or pentests because it can sometimes give you wrong info and send you down rabbit holes. Some people suggest sticking to regular search engines and reliable sources like software documentation instead.
Personally, I think ChatGPT is a great addition to my pentesting process. It helps me find information way faster and easier than regular search engines. Plus, it can whip up scripts and small tools almost instantly, even if I need to tweak the code a bit. But it’s important to remember that ChatGPT can easily make stuff up, especially on less common topics or if you lead it in a certain direction.
For instance, during the exam, I was stuck on something unfamiliar and wasn’t sure if an idea I had was worth trying. I asked ChatGPT, and it confidently told me my idea wouldn’t work, with some rather convincing arguments. This threw me off for a bit, but further research (using regular search engines) made me question its response. I decided to go with my idea anyway, and it worked, helping me move forward in the exam.
Treat ChatGPT as a more ergonomic search engine with an increased likelihood of giving false information. Don’t treat it like an all-knowing oracle, and always use your own judgment.
Think dumber
This is a common mantra you’ll see repeated in the Discord server and other places where discussions about the exam occur. The message is not that you should turn off your brain, as the exam is very demanding and will test your memory, pattern recognition, creative thinking, and more.
Instead, it’s a warning that, because the exam is so challenging, any minor obstacle might lead you to overthink and create elaborate solutions when sometimes the answer is much simpler. It’s a good idea to rank your solutions by complexity and try them in order from simplest to most complex. There will definitely be times when the solution to a problem is very complex and will push your skills to the fullest, but make sure you’re not wasting time on a minor problem.
Go for the low-hanging fruits first, then attempt the complex multi-step exploit chain.
Don’t go for flags 13 and 14 until you are satisfied with the report
To pass the exam, you must meet both of the following criteria:
- Capture and submit at least twelve out of the fourteen available flags.
- Produce a commercial-grade report covering the pentest that meets the grader’s standards.
If you fail to meet either criterion, you fail the exam. Most hackers prefer tinkering with computers and pwning systems over writing detailed reports in corporate-speak, so it’s common to procrastinate on the reporting portion of the exam. As I said before, this is a mistake. More importantly, pursuing the last two flags after you have the minimum twelve doesn’t make sense unless you already have a flawless report. There is no additional benefit to getting all fourteen flags; your certification will be the same as anyone else’s, and there is no hidden reward for capturing every flag. Frankly, it’s puzzling to me why these last two flags exist at all.
Unless you’re taking the exam purely for fun, you’re likely doing it for the benefits the certification will bring to your personal or professional life. Since you’re not just messing around, any effort spent capturing the last two flags would be better invested in perfecting your report. The flag criterion is objective and straightforward, but report quality is subjective, and you can never be certain your report will meet the grader’s standards.
Once you are satisfied with your report and reasonably confident it will pass, then you can go after flags 13 and 14 for the bragging rights. Until then, focus on the report and secure the win.
Remember you have a second attempt, but don’t expect nudges
Every exam voucher you buy gives you two attempts at the exam. If you don’t get the minimum of twelve flags on your first attempt or fail at the report, you can have a second go at no extra cost. The catch is that you need to start your second attempt within two weeks (fourteen days) of receiving feedback from your first attempt, which can take up to twenty business days. Most people need both attempts to pass, so if your schedule allows, you can treat this as a twenty-day-long exam with a nice break in the middle, potentially just over a month long. In my opinion, that’s way too much downtime, so I’d recommend aiming to finish the exam in just one attempt if you can.
Now, about the exam feedback if you fail an attempt. There are anecdotes claiming that the feedback might include small hints or nudges toward the flags you missed, like recommendations on which modules to review for your next attempt. However, I’ve seen more warnings from people saying that the feedback only concerns the reporting portion of the exam and won’t help you with the flags. I can’t speak from experience, but I find it hard to believe that HTB would give out anything resembling a hint, especially given how serious they are about preventing cheating and sharing exam information. Even if they did, the uncertainty means it’s better not to expect any help in case you fail, as relying on that possibility could become a mental crutch.
In short, remember that you have a second exam attempt free of charge, which should help alleviate some pressure. But don’t expect any help from the graders if you fail an attempt; you’re on your own.
