- Check this post for my overall experience on the exam and what I learned from it.
- Check this post for general tips and tricks for the exam and its preparation.
- Check this post my methodology for report writing for the exam.
Introduction
On June 21st, I submitted my exam for Hack The Box’s Certified Penetration Testing Specialist (HTB CPTS), which is an intermediate-level certification for pentesters and ethical hackers. It was ten intense days of exploiting vulnerabilities, gathering information, and pivoting around a simulated enterprise network. Besides all the hacking, there was quite a bit of writing too, as the certification requires not only the submission of various “flags” hidden within compromised systems but also the creation of a commercial-grade report, which is also graded.
And although the exam itself was extremely challenging, it was merely the capstone of a months long journey of studying and preparing to take it. To even attempt to the exam, the candidate must also complete 100% of the Hack The Box Academy’s Penetration Tester job-role path.
I used the Android app Goodtime to study with the Pomodoro technique: 25 minutes of focus, 5-minute breaks, and a 15-minute break every four sessions. The app also lets you label your study sessions and export time stats to a CSV. This helped me keep detailed logs of my study time for the CPTS, so I made this post to share what I found.
This post is set up like a Q&A with questions commonly seen on places like the Hack The Box Discord server, featuring a TL;DR section for each question if you’re looking for a quick answer.
Q&A
What was your CyberSec experience prior to taking the course?
TL;DR: Bachelors in Software Engineering, all offensive learning paths on TryHackMe and a few dozen easy and medium THM boxes.
By the time I started the job-role path, I had been a Software Engineering graduate for a few months. While my degree wasn’t heavily focused on cybersecurity, I did take a class on the fundamentals of information security, which covered mostly blue team topics, as well as cryptography and communication protocols.
In addition to that, I had completed all the offensive learning paths from TryHackMe, which are Red Teaming, CompTIA Pentest+, Offensive Pentesting, Jr Penetration Tester, Web Fundamentals, Introduction to Cyber Security, and Pre Security.
I also done quite a few easy and medium boxes on TryHackMe, mostly focusing on Linux machines, enough to the top 100 leaderboard in my country. However, I hadn’t done a single Hack The Box CTF box at that point.
So, while I wasn’t brand new to offensive security, I wasn’t an expert or even an intermediate. I was a beginner with some CTF experience.
What are your overall feelings about the path?
TL;DR: Excellent material, strongly recommend even if you don’t plan on taking the exam.
Taking the Penetration Tester path was hands down the most effective way I’ve improved my hacking skills, even more than all my other tech experiences combined. The material is incredibly well-structured and covers everything comprehensively. Even if you’re not planning to take the exam, I’d definitely recommend going through the learning path just to level up your skills.
I’m usually cautious about recommending paid resources when there’s so much good free content online, but in this case, I genuinely believe it’s worth the investment. It offers unmatched value for anyone serious about getting into pentesting.
How long did it take you to complete the path? How long did you study each day?
TL;DR: I finished the path over five months, including a two-month break. Daily study time varied, averaging a little over two hours, increasing as I progressed.
I started the CPTS path right after New Year’s Eve, starting on January 2nd, 2024. I stayed consistent, studying almost every day until early February. Then, I took a solid two-month break for vacations and to focus on a job opportunity. Come April, I got back into it and kept at it almost daily until June 6th, when I completed the final module.
All in all, it took me 156 days to complete, which is just over five months. But I was actively studying for only about 105 of those days, roughly three and a half months.
This also includes time spent on modules that are recommended but not part of the path, like Learning Process, Windows Fundamentals, Introduction to Active Directory, and Using CrackMapExec.
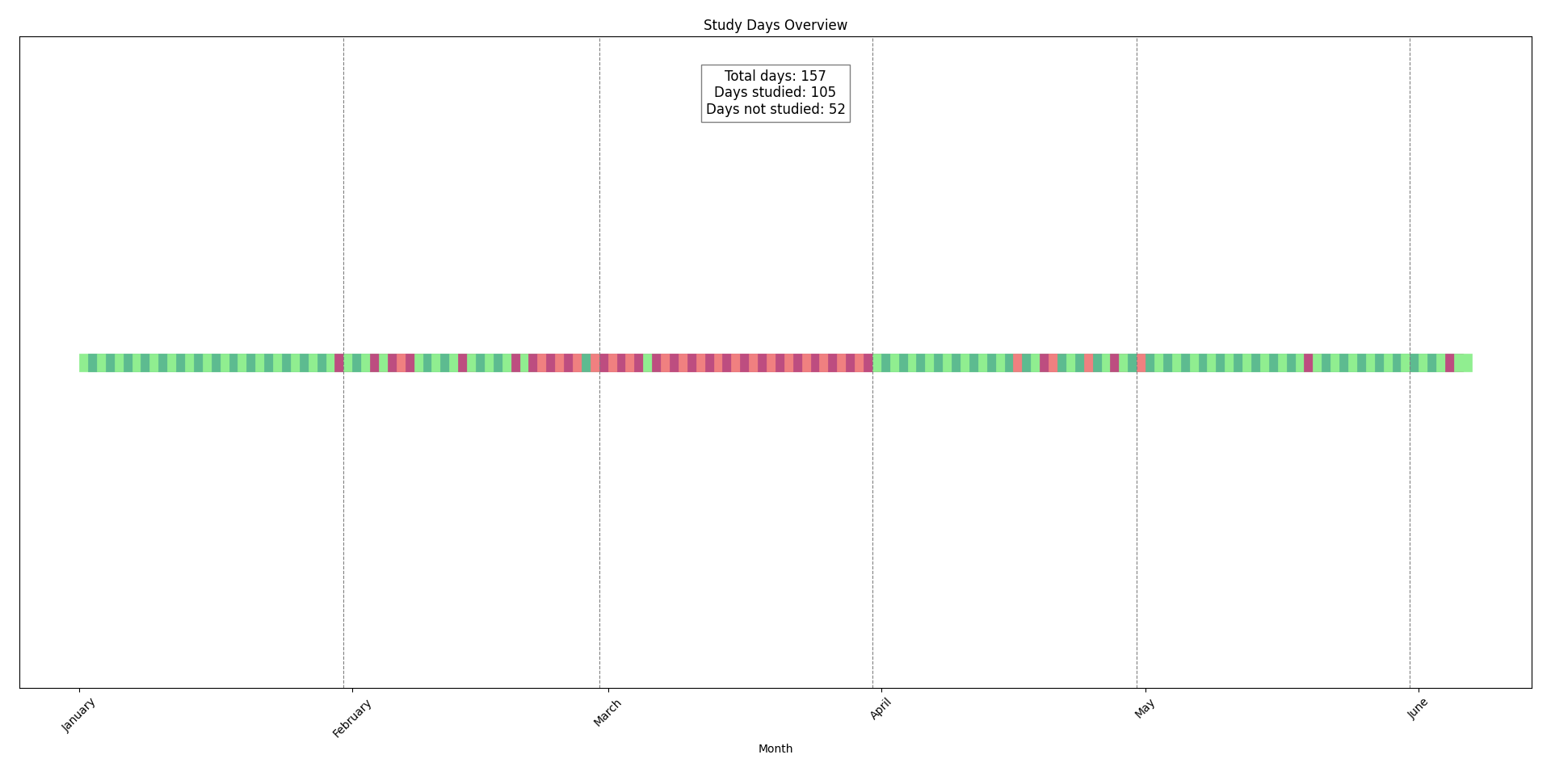
Days studied
My daily study hours varied quite a bit, averaging around 2.47 hours per day, with a median closer to 2.18 hours. This might seem low for someone studying full-time, but I only logged focused, quality study time—not time spent on breaks or waiting for commands to run. I didn’t force myself to study a set number of hours daily; I aimed for at least two, but if I felt unproductive or disengaged, I took a break. As I progressed deeper into the course, I naturally found myself studying more each day.
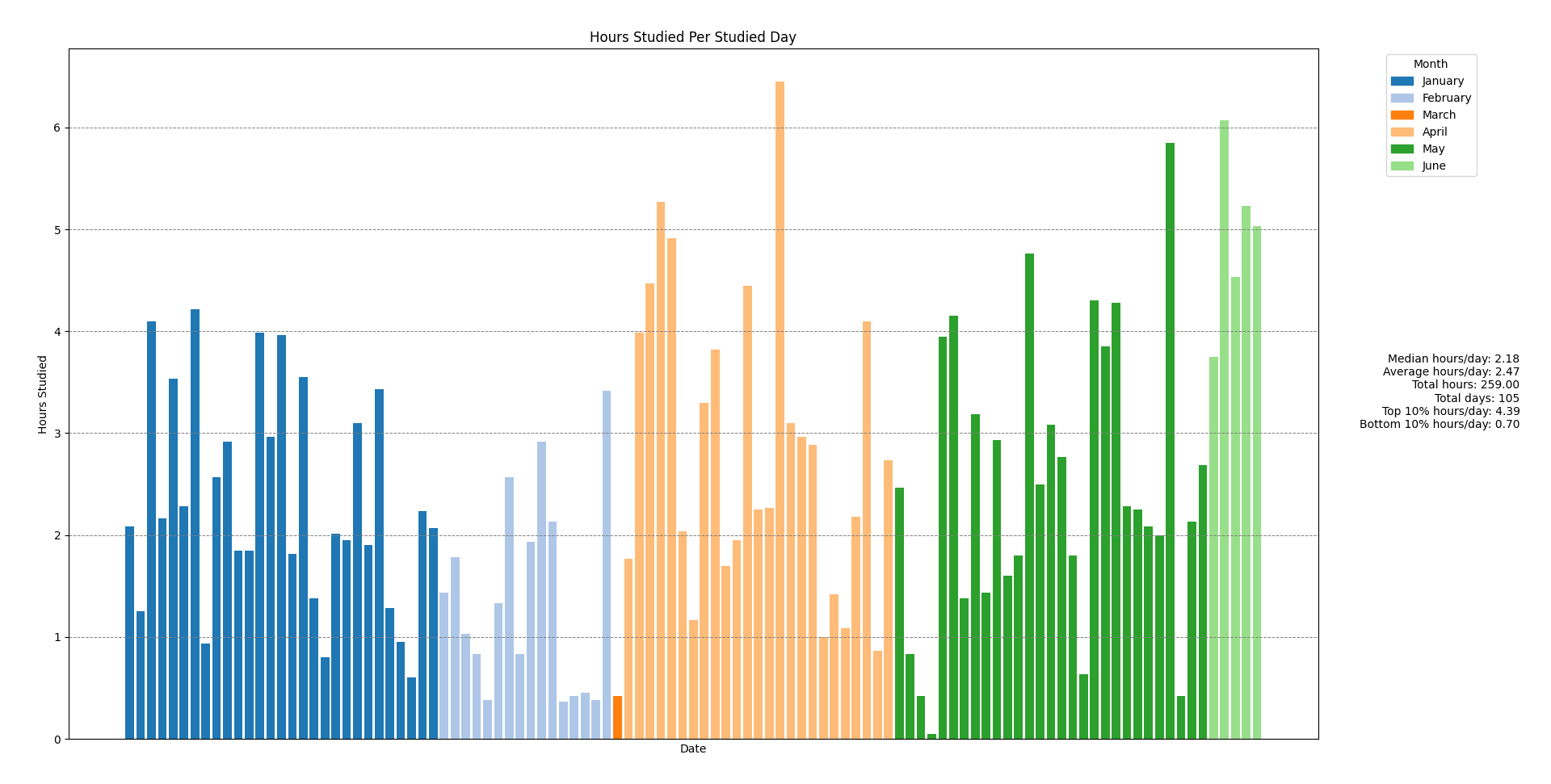
Hours per day studied
Do you think the 43-day estimate is accurate?
TL;DR: If taken literally, nope, too optistimic. In terms of hours, it actually took less time in my case.
The course gives an estimation of 43 days to finish it, but that seems odd because how long it takes really depends on how much you study each day. Hack The Box counts a “day” as an 8-hour study session, so the 43-day estimate actually means you’re looking at around 344 hours of study time.
For me, it ended up taking roughly 259 hours to complete the main path and some of those extra modules I mentioned earlier. That’s about 24.65% less than what they estimated. Their estimation seems to have been a bit off, but it’s worth noting that I didn’t complete some of the recommended extra work, such as a specific number of HTB machines or pro-labs.
But if we take the 43 day estimation at face value, then I believe it is not realistic at all. Even though I made studying for the exam my top priority for over three months, I never once managed to put in a solid 8 hours of study time a day. I don’t think many people could keep that up for six weeks straight without burning out. It might work if you already know most of the topics and are just cruising through the material, but for regular learning, it’s a stretch.
How long did you spend on each module? Were the time estimates accurate?
TL;DR: The estimations were mostly accurate, though they tended to overestimate a bit. The password attacks module took significantly longer than expected.
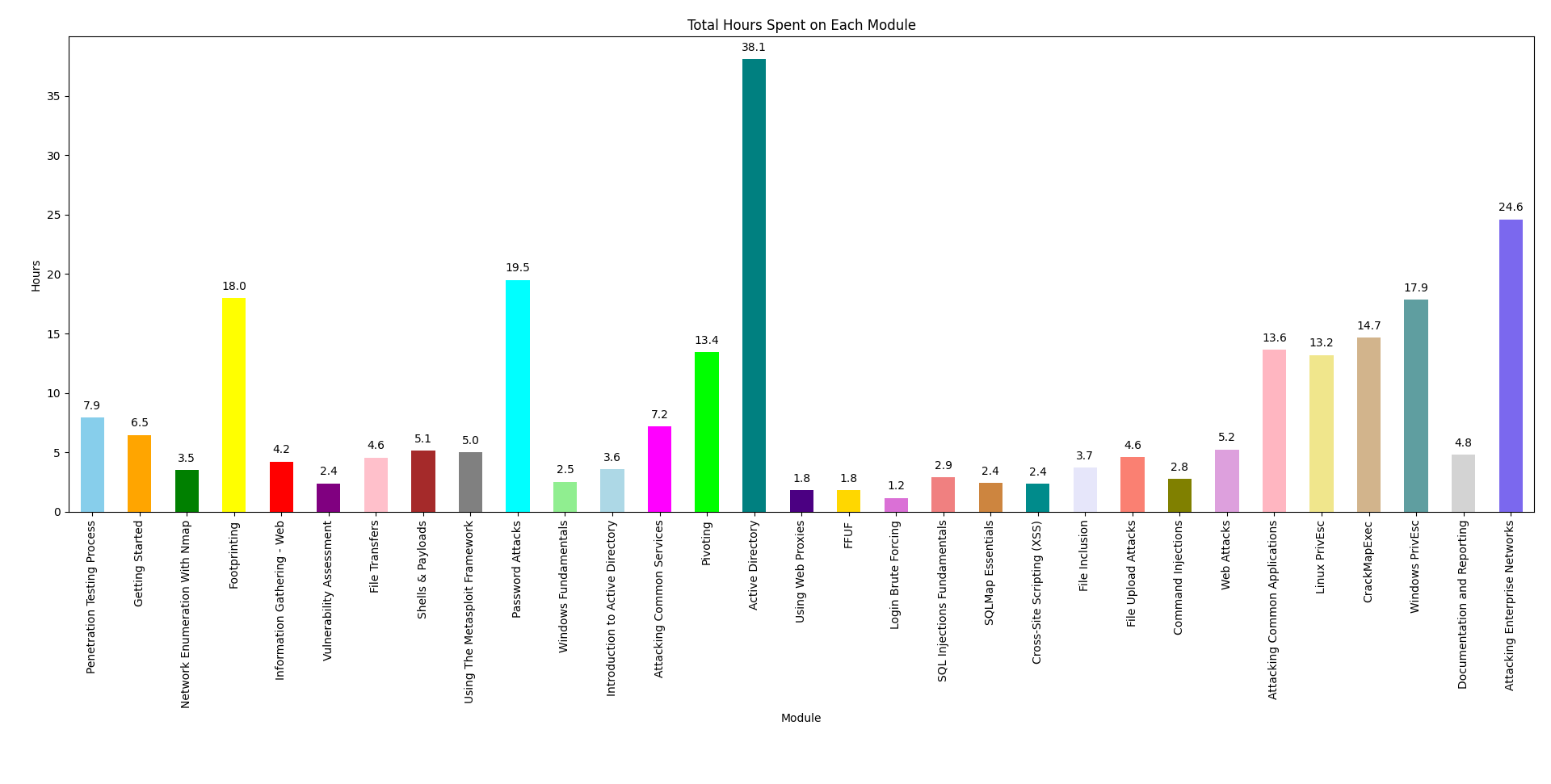
Hours per module
The module time estimates were usually a bit longer than what I actually spent. Sometimes I breezed through modules because I was already familiar with the topics and focused on note-taking and organizing.
Estimation comparasion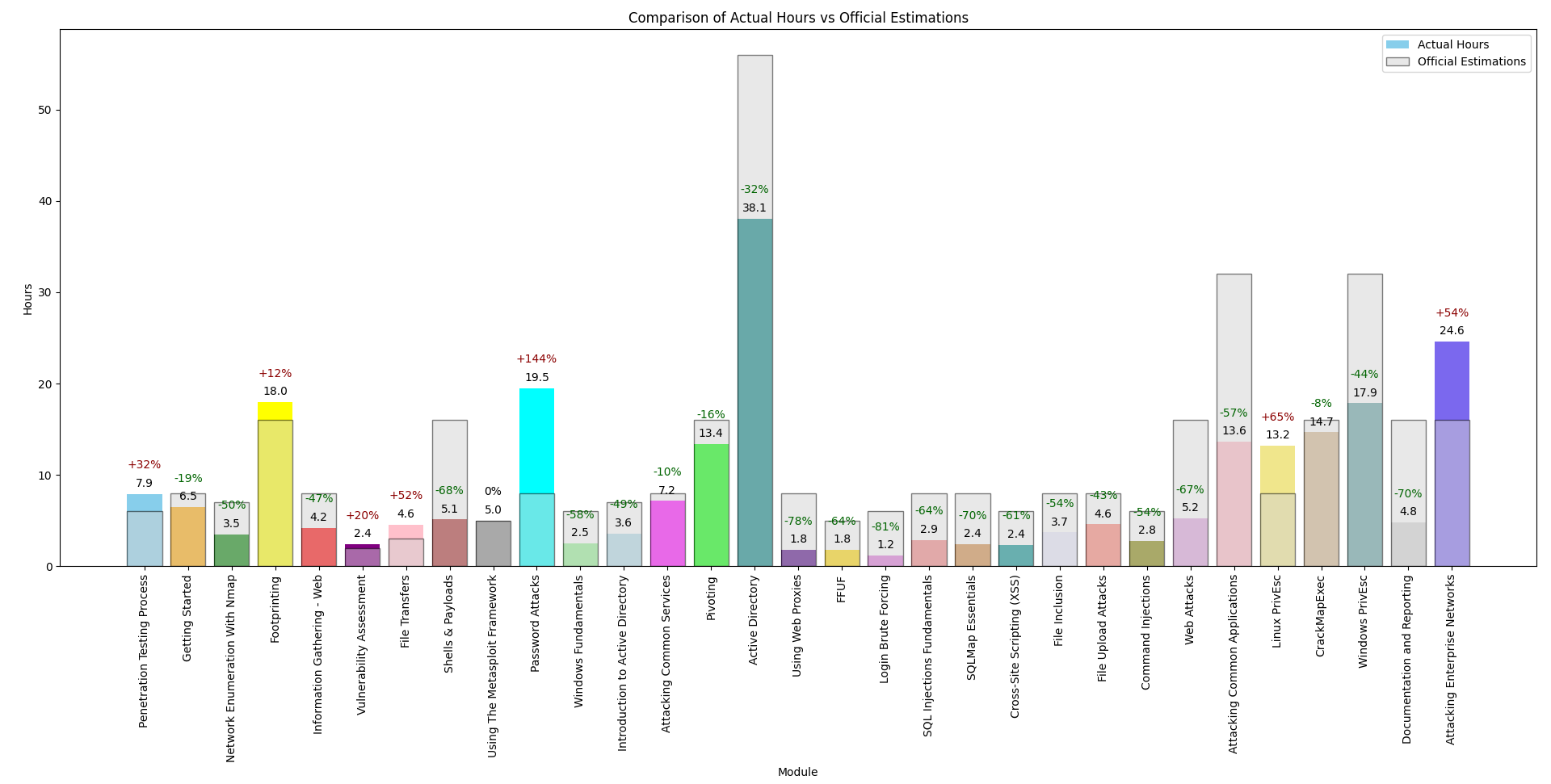
The Password Attacks module was the big outlier, taking a whopping 144% more time than estimated. And that’s not counting the wait time during brute force attacks, which added even more. That module was a real drag.
Next, the Active Directory Enumeration & Attacks module took the longest of any module, but still considerably less time than officially estimated.
The Documentation and Reporting module was quicker than estimated because I didn’t do a full report for the skill assessment. I’ll go into my reporting approach more in another post.
Lastly, the Attacking Enterprise Network module took longer than estimated, but I approached it blindly. I started the lab without reading the questions or walkthroughs, trying to achieve domain compromise without any guidance. This method is a popular way to gauge readiness for the exam, and I’ll cover more exam tips in another post.
What were your favorite and least favorite modules?
The modules I thought were the most informative and/or of higher quality were:
- Attacking Enterprise Networks - This is like a mock exam you can attempt blindly and then follow the walkthrough to see what you missed. It’s invaluable for testing how solid your methodology is before attempting the actual exam.
- Penetration Testing Process - This is a high-level overview of the path given at the very start. I love knowing what I’ll be studying before I start, so I found this super useful.
- Active Directory Enumeration & Attacks - Comprehensive and structured in a way that’s easy to consult during a pentest.
- Documentation and Reporting - Since the exam requires you to submit a commercial-grade report to pass, this is one of the most important modules of the path.
- Using CrackMapExec - As far as I know, this isn’t mentioned or recommended anywhere in the path itself, but it’s one of the most useful modules you can take before the exam.
The modules that disappointed me the most were:
- Password Attacks - Mostly involved sitting around waiting for brute force attacks to succeed, which took several minutes.
- Shells & Payloads - The material felt lower in quality compared to the rest. It also covered topics better discussed in other modules and didn’t feel like it belonged in the path.
- Linux Privilege Escalation - I had high expectations, but it focused more on individual LPE vectors than on a cohesive methodology for privilege escalation. The notes I developed through my CTF boxes were more complete than what was covered in the module.
- Vulnerability Assessment - Just a bit boring.
Overall, even the modules I found to be of lesser quality were still pretty good.
How much did the course cost you?
TL;DR: 40€ with the student plan, could have been 24€ had I canceled the plan when I was not studying.
I was eligible for the student subscription at Hack The Box Academy, so I paid just 8€ a month for access to all modules Tier II and below, which includes the entire CPTS path.
I kept the subscription active during the entire five-month period, so it cost me 40€ for the whole path, which was a bargain. If I had thought to disable my account for the two months when I wasn’t studying, I could have saved 16€, but it is what it is. I definitely recommend checking if your university is eligible for the student discount.